Hack the Box - Penetration Testing
Hack The Box (HTB) is an online platform that offers a variety of virtual labs and challenges for cybersecurity enthusiasts and professionals to test and enhance their hacking skills in a legal and ethical environment. It provides a safe and controlled space for users to practice and improve their penetration testing and cybersecurity knowledge.
I use a Kali Linux virtual machine on Hyper-V for my HackTheBox labs. Hyper-V comes with Windows Professional versions but Virtual Box or any other virtual machine manager would work as alternatives.
Using virtual machines offers several advantages, especially in the context of cybersecurity. Virtual machines provide complete isolation from the host operating system. This means that any changes made within the VM do not affect the host system, and vice versa. VMs support snapshot and rollback functionality. You can take snapshots of a VM at various stages of testing, and if something goes wrong or the system becomes unstable, you can easily revert back to a previous snapshot.
Kali Linux is a specialized Linux distribution designed for penetration testing, ethical hacking, and cybersecurity tasks. Kali comes pre-installed with a vast collection of tools and software for various aspects of penetration testing and security assessment.
There are many machines that can be used to begin with from the starting point section that include complete walk throughs on how to root the box. Having access to the target machines requires tunneling into HackTheBox’s lab network. The VPN configuration file can be downloaded from HackTheBox and used with OpenVPN within the virtual machine.
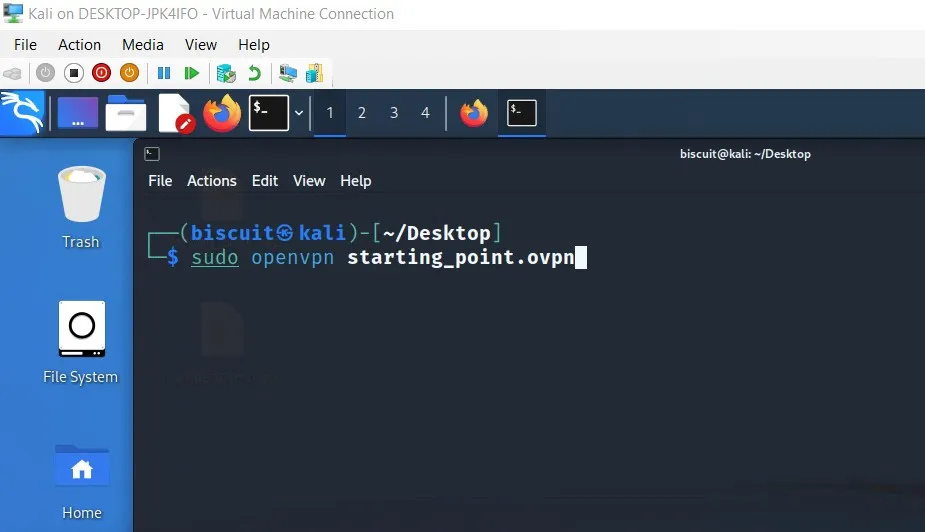
I run a tabbed terminal emulator with one tab being dedicated to the OpenVPN process running with the VPN config file downloaded from HackTheBox.
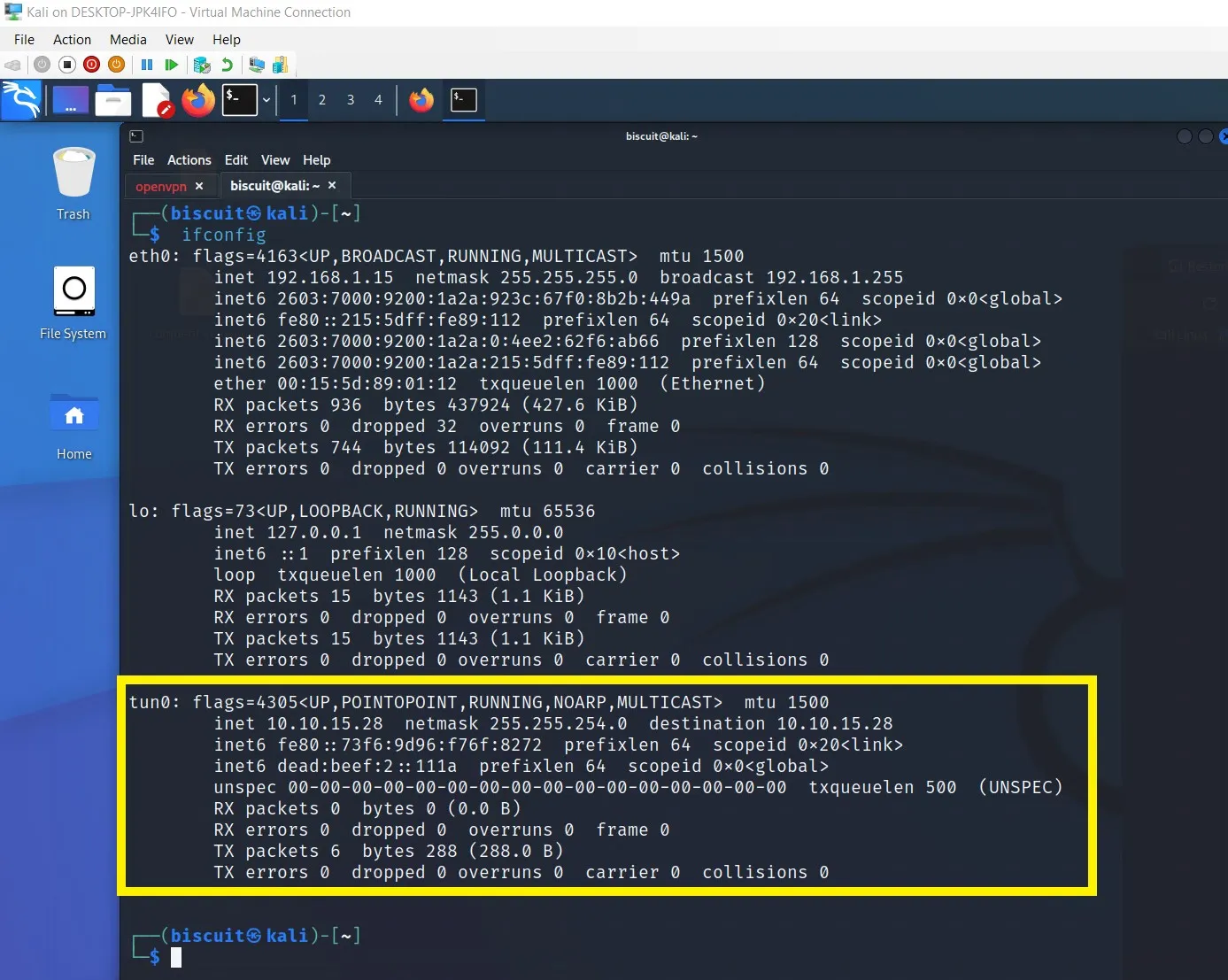
Once connected through a VPN connection, running the “ifconfig” command will display a tunnel interface and its assigned internal IP address used within HackTheBox’s lab network.
After connecting via VPN, a machine can be selected from the catalogue to target. Its internal IP address will be displayed.
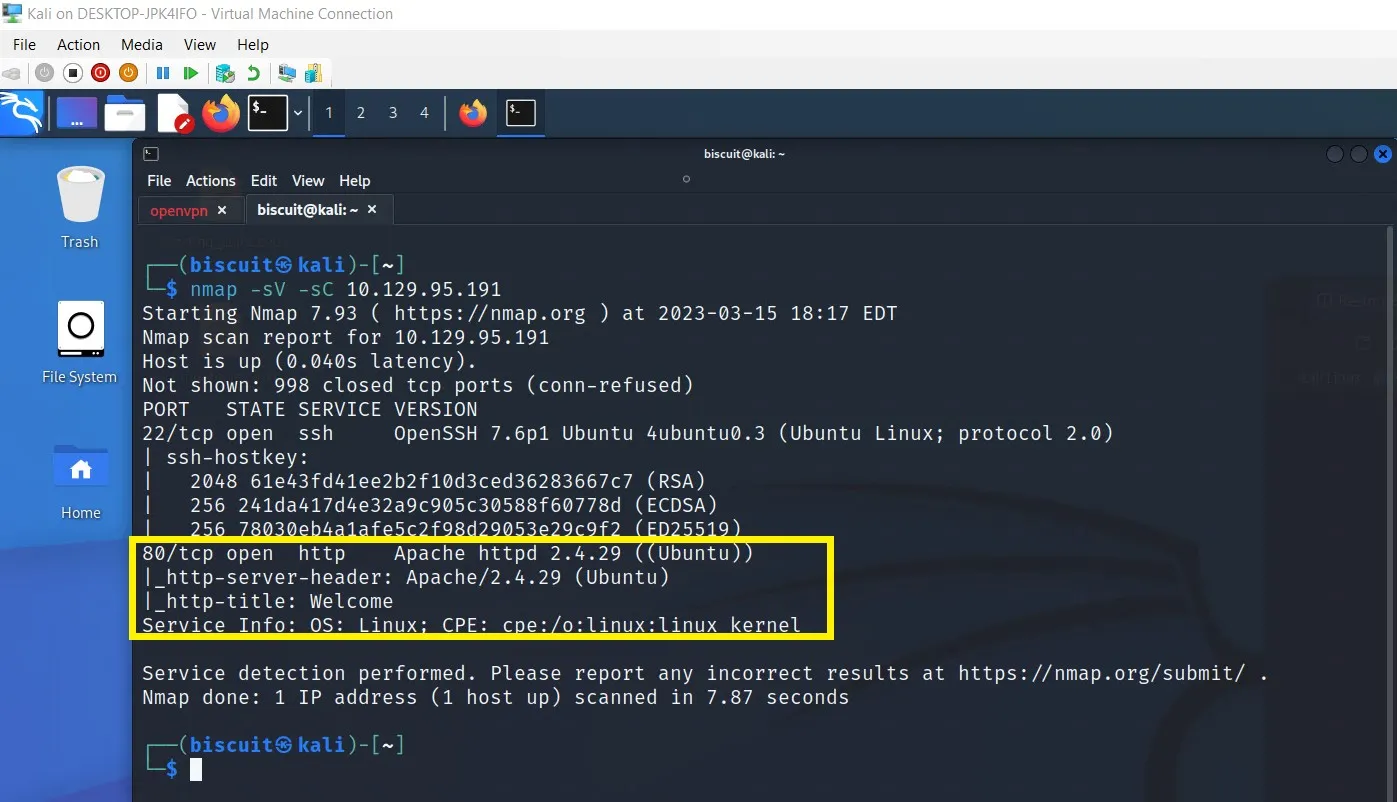
Almost every penetration test will begin with a port scan to see what services are running or being hosted on the target machine. These discovered open ports will then be prioritized by the likelihood of being comprimisable and then actively probed to search for potential vulnerabilities.
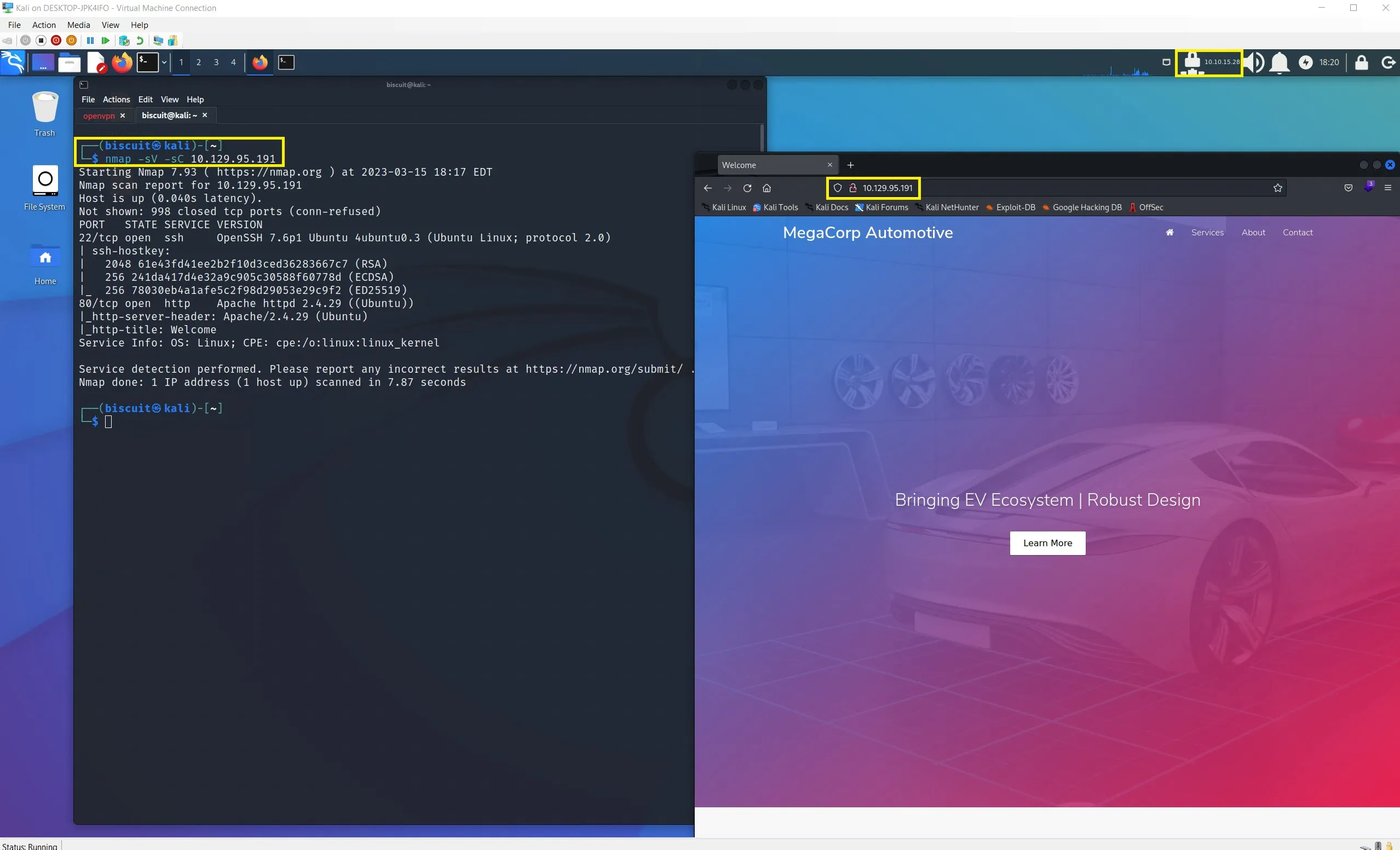
Though not all machines will be running a web server, many of them from HackTheBox will. This portion will put to practice web application penentration testing methologies and common techniques that target the most common web app security risks defined in the OWASP Top Ten.
Most machines will follow the strategy:
- Compromise the web app.
- Use the compromised web app to gain more information about the machine.
- Gain access to a user account.
- Find and use a privilege escalation vulnerability to exploit and get root user permissions.
The goal of these machines is to capture the flags. The flags are files stored within the machines at two different account levels, user and root. One flag will be stored in a regular user folder, and the other within the root user’s directory which will require administrator permissions to read.
Happy Hunting!